The Kerberos protocol defines how clients securely interact with a network authentication service. It allows clients to obtain tickets from the Kerberos Key Distribution Center (KDC), which they use to authenticate themselves to application servers when establishing connections.
Kerberos operates using tickets to authenticate users and entirely avoids sending passwords across the network, thereby enhancing security and reducing the risk of credential theft. Instead of transmitting passwords, the protocol relies on encrypted ticket exchanges for authentication.
Kerberos functions over port 88, which is reserved for its communication. When we observe traffic directed to destination port 88, it typically indicates that an authentication process is taking place.
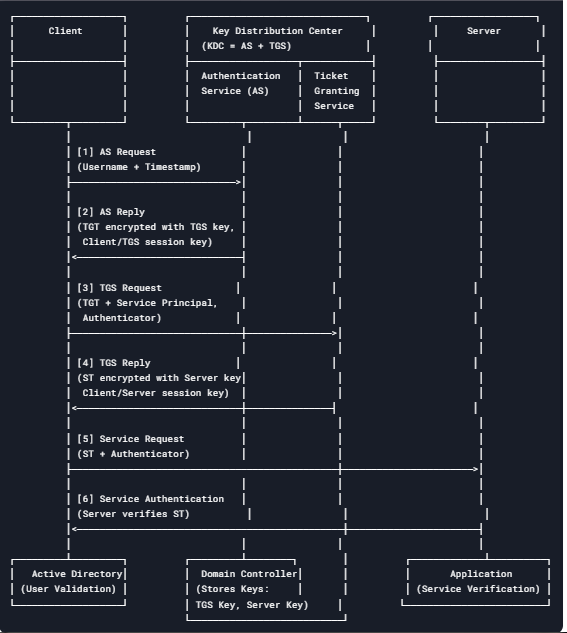
Step 1:
The client begins the authentication process by sending a request to the KDC (Key Distribution Center). it contain • Username of the client to be authenticated.
Step 2:
The KDC checks its database, which contains hashes for users, the special Krbtgt account, and service accounts, to verify the client’s identity.
Step 3:
Once the KDC verifies the client, it sends a Ticket-Granting Ticket (TGT), which the client stores in its memory (sometimes referred to as the “Kerberos tray”). The TGT is used to identify the client for future requests. The client then sends a copy of the TGT, along with some encrypted data, back to the KDC to request access to a specific service.
Step 4:
The KDC receives the request for a Ticket-Granting Service (TGS) and decrypts the message using the Krbtgt hash (this is like unlocking it with a special key). The KDC then sends back a TGS encrypted with the service’s hash (locked with a different key), along with some encrypted data containing information about the user.
Step 5:
The client then forwards the TGS to the Application Server, which can decrypt it and use it to grant access to the requested service.
