What is Phishing? How Are Phishing Links Created and Shared with Victims? How Can You Identify and Protect Yourself from Phishing Attempts?
 1.What is phishing?
1.What is phishing?
Phishing is a type of cyber-attack where criminals impersonate legitimate organizations or individuals to deceive victims into revealing sensitive information, such as usernames, passwords, credit card details, or other personal data. It usually occurs through fraudulent emails, messages, or websites that appear trustworthy.
2.How Phishing Links are Created and Shared with Victims
Phishing links are often created by cybercriminals to appear like legitimate URLs from trusted sources. These links are typically shared via:
- Emails: Attackers send emails that look like they come from a legitimate company or service, urging victims to click on a link. Once clicked, it may direct them to a fake website designed to collect personal information.
- SMS or social media: Phishing attempts can also occur through text messages or social media platforms, where attackers try to lure victims into clicking malicious links.
- Fake Websites: The phishing link often leads to a counterfeit website that looks identical to a legitimate one, but it’s designed to steal the victim’s sensitive information when entered.
There are many methods to create phishing links. Let’s go through one of the methods for understanding:
Below is a video sample showing how attackers create a phishing link:
3.How Do They Get Your Email Address?
Think of your email address like your online home address. Bad guys need it to send their fake “mail.” They might get it in a few ways:
- Out in the Open: Sometimes, we accidentally leave our email addresses in public places online, like on social media profiles or in comments on websites. It’s like leaving your front door slightly ajar.
- Bought and Sold Lists: Believe it or not, there are shady folks who collect lists of email addresses and sell them to others, including these attackers. It’s like your address being put on a spam mailing list, but much worse.
- From Old Hacks: If a website or service you used got hacked in the past, your email address might have been stolen. These stolen details can then be used for phishing.
Below is the video reference to check if your email has been leaked anywhere:
4.Then, How Do They Send Those Fake Emails with the Links?
Once they have your email, they need to send the fake email containing the dangerous link. Here’s how they might do it:
- Using Special Sending Tools: Just like companies use software to send out newsletters, attackers use tools to send out lots of fake emails at once. These tools help them manage many emails and send the same convincing-looking message to lots of people.
- Building Their Own Trap (The Phishing Link): The tricky part is the fake website. Attackers often create these themselves. It looks just like the real login page for your bank, social media, or another important website. This is the “phishing link” – their trap.
- Putting the Bait in the Email: They then put this fake link inside the email they send to you. The email will usually try to scare you or make you feel like you need to click right now. They might say your account is locked or there’s a problem you need to fix urgently.
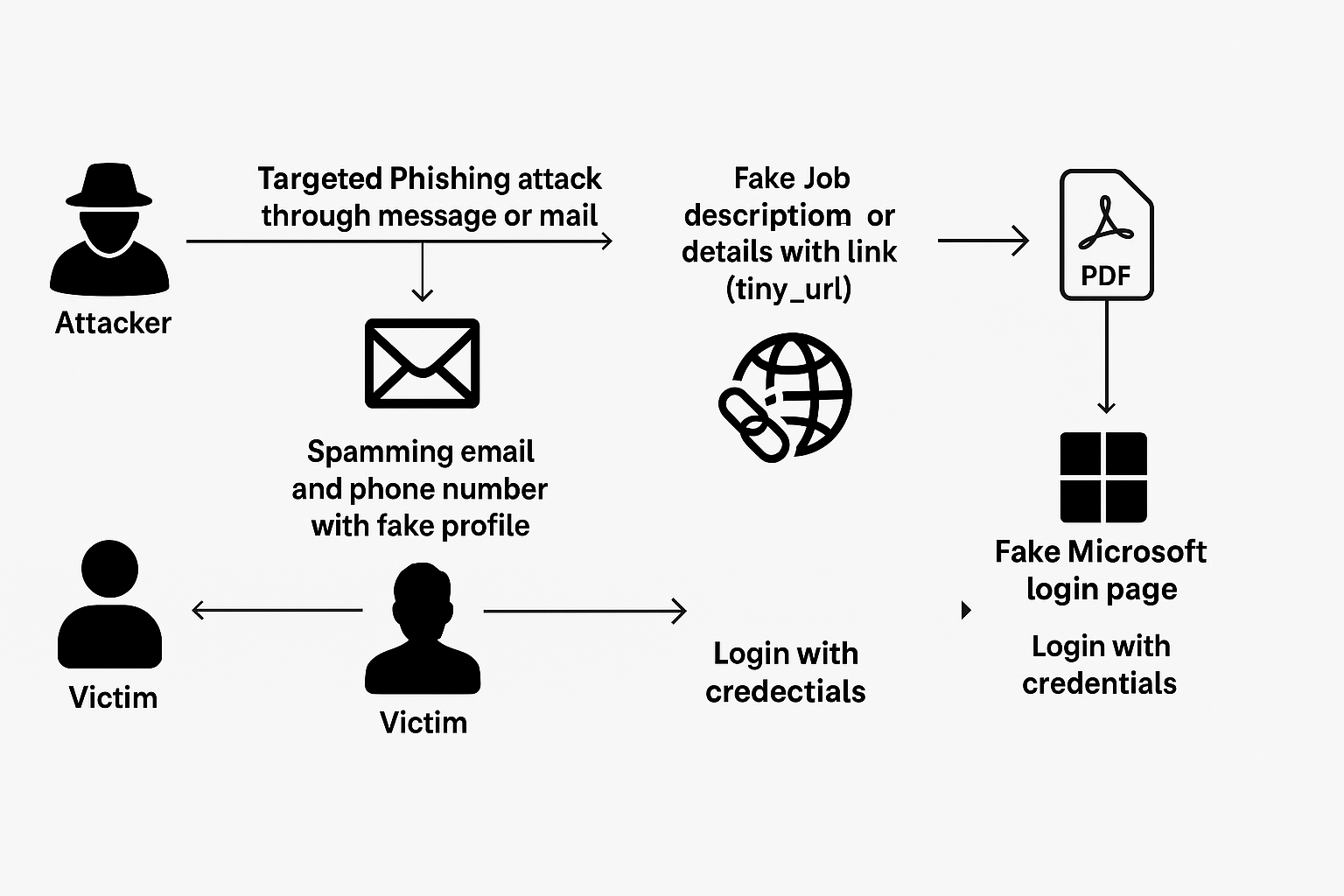
We have created a fake phishing link as shown above. Using that link, we will send an email to the victim, encouraging them to click on it. Below is a sample video demonstrating one of the methods used to share the phishing link. There are other ways to distribute it as well, using tools like GoPhish, King Phisher, and more.
Once a user clicks this phishing link, the attacker will get details on their server.
Let’s take one example the attacker sends a fake job offer link to the victim using email or message, often hiding the real link with a short URL.
When the victim clicks the link, they’re taken to a fake Microsoft login page. Once they enter their details, the attacker steals their login credentials.
5.How to Identify Phishing Attempts
Suspicious Sender Email or Phone Number
- Check the sender: Even if it looks like it’s from a known company, the email address might be slightly off.
👉 Example: support@paypall.com instead of support@paypal.com.
Urgent or Threatening Language
- Scammers create panic to make you act fast. 👉 Example: “Your account will be suspended in 24 hours unless you verify now.”
Unusual Links or Attachments
- Hover over links to preview the URL. If the address does not match the real domain, don’t click.
👉 Try This: In Gmail or Outlook, hover your mouse over the link without clicking—check if it points to a suspicious domain.
Poor Grammar and Spelling
- Many phishing emails contain awkward language or typos. 👉 Red Flag: “Dear Costumer, you acount has been compromised.”
Generic Greetings
- Real services usually use your name. 👉 Phishy: “Dear user” or “Hello customer” instead of your actual name.
Too Good to Be True Offers
- If an email promises free money, gifts, or prizes out of nowhere—it’s bait. 👉 Example: “Congratulations! You’ve won a $500 Amazon gift card!”
6.How to Protect Yourself from Phishing (Quick Tips)
✅ Don’t Click Suspicious Links: Avoid clicking on links in unexpected emails or messages. Instead, type the website URL directly into your browser (e.g., paypal.com).
✅ Enable Multi-Factor Authentication (MFA): Turn on MFA wherever possible to add an extra layer of security beyond just your password.
✅ Use a Password Manager: Password managers help you use strong, unique passwords for every site—and they won’t autofill on fake or phishing sites.
✅ Keep Software Updated: Always keep your browser, operating system, and antivirus software up to date to patch known vulnerabilities.
✅ Report Phishing Attempts: Report phishing emails using your email provider’s “Report phishing” feature or forward them to reportphishing@apwg.org
