What is Explorer.exe?
According to STZ, explorer.exe is a executable which comes into picture when ever end-user interact with the computer system.
Critical Ports
A Critical Ports refers to a network ports that are important for the functioning, security, or accessibility of a specific system or service.
What is Phishing
What is Phishing? How Are Phishing Links Created and Shared with Victims? How Can You Identify and Protect Yourself from Phishing Attempts?
Port Scan vs Port Sweep
Port scan and Port Sweep both are the part of the reconnaissance phase.
This is very initial stage for an attacker to know about the system.
Static Malware Analysis
Malware analysis is a critical process in cybersecurity, enabling analysts to understand malicious software's behavior, functionality, and objectives.
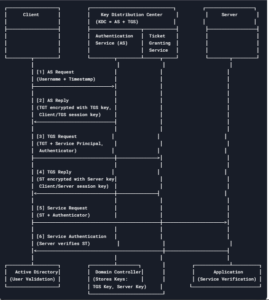
Kerberos Authentication Protocol
The Kerberos protocol defines how clients securely interact with a network authentication service. It allows clients to obtain tickets from the Kerberos Key Distribution Center (KDC),